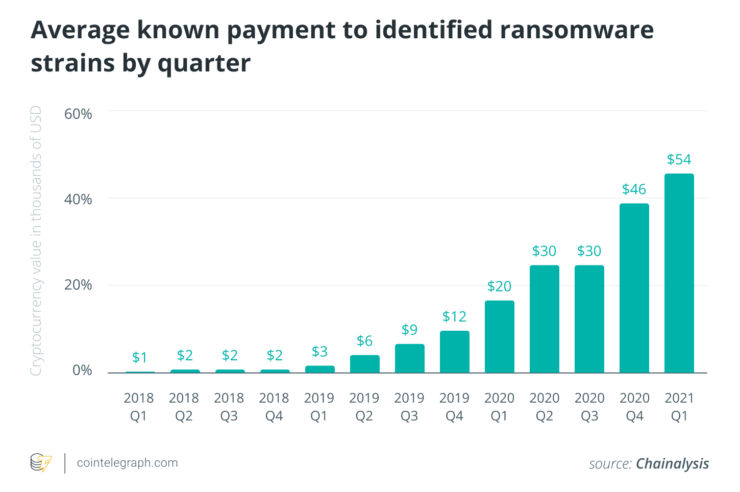
Just between July 2020 and June 2021, ransomware activity soared by a whopping 1,070%, according to a recent Fortinet report, with other researchers confirming the proliferation of this mode of extortion. Mimicking the prevalent business model of the legitimate tech world, ransomware-as-a-service portals popped up in the darker corners of the web, institutionalizing the shadow industry and slashing the skill ceiling for wannabe-criminals. The trend should be ringing a warning bell through the crypto ecosystem, particularly since ransomware attackers do have a knack for payments in crypto.


That said, the industry that was once a Wild Wild West is now assuming a more orderly setting. Slowly but surely infiltrating the mainstream, it is now at the point where some of the largest centralized exchanges (CEXs) are hiring top-notch financial crime investigators to oversee their efforts against money laundering.
The problem is that not all exchanges are made equal. A centralized exchange works in many of the same ways a traditional business entity does, but this is not to say that all of them are now lining up to get their Anti-Money Laundering (AML) right. Things get even trickier with decentralized exchanges (DEXs), which, let’s face it, are not as decentralized as the name implies, but like to claim otherwise. In most cases, DEXs have little, if anything, in terms of Know Your Customer (KYC) measures, helping users hop between coins and blockchains at their leisure while leaving few traces. While some of them may utilize various analysis services to do background checks on wallets, hackers can try making their way around those by using mixers and other tools.
Related: DAOs are meant to be completely autonomous and decentralized, but are they?
As far as ransomware cash flows go, both DEXs and CEXs are very much on the radar — but criminals use them for different purposes. Criminals use DEXs, along with mixing services, to launder the ransom paid by clients, moving it from address to address and from currency to currency, according to a recent report by the U.S. Financial Crimes Enforcement Network. CEXs, for their part, mostly work as the exit point for criminals, allowing them to cash out coins into fiat.
Related: Crypto in the crosshairs: US regulators eye the cryptocurrency sector
Having stolen money moved through your network is not a good look for anybody, and sometimes, it comes with consequences. Just this September, the U.S. Treasury slapped sanctions on OTC broker Suex for effectively working to facilitate ransomware money-laundering. The exchange was nested on Binance, though the company said it had de-platformed Suex long before the Treasury’s designation based on its own “internal safeguards.”
The development should be a wake-up call for both CEXs and DEXs everywhere, as it applies the domino effect of U.S. sanctions to the crypto ecosystem. A sanctioned entity may be sitting comfortably in its home jurisdiction, but in the current interconnected world, U.S. sanctions hamper operations involving foreign clients it may wish to undertake even more. It just does not have to involve only Binance — it could include any legitimate business with a U.S. presence and interests, and the same goes for hosting providers, payments processors or anyone enabling the day-to-day business operations of the target company.
Hypothetically, sanctions could even indirectly affect decentralized entities in a myriad of ways. Decentralized projects still normally have core dev teams associated with them, which invokes the prospect of individual responsibility. In the future, and with enough regulatory rigor, they could one day even see their incoming and outbound traffic throttled or outright blocked by IPSes unless users utilize extra obfuscation tools like VPN.
Related: From NFTs to CBDCs, crypto must tackle compliance before regulators do
Attrition war on ransomware
The Suex OTC incident and its far-reaching implications point us at what could be a larger strategy for smothering ransomware groups. We know they are dependent on multiple nodes inside the crypto ecosystem, but DEXes and CEXes hold special value in their eyes by enabling them to hide their tracks and put hard cash in their pockets. And that’s the end goal, in most cases.
It is naive to expect every player in this field to be equally diligent with their internal safeguards. Enforcing standards for KYC and AML across exchanges will, at the very least, make it harder for criminals to move crypto around and cash out. Such measures would amp up their losses, making the entire operation less profitable and, thus, less lucrative. In the long run, ideally, it could deny them vital areas of the vast infrastructure they use to haul the money around, making the cookie jar effectively inaccessible. And why pursue money you can’t put in your pocket?


With advances in machine learning and digital identification, DEXes can be as apt in KYC as their centralized kin, using AI to process the same documents that banks would for their KYC efforts. It’s a procedure that can be automated, giving their legitimate customers more peace of mind and, potentially, draw in more cash flows with their regulated status. The crypto community could tread even further by implementing extra checks on transactions involving exchanges and services known to have a heavy proportion of illicit activity. Even though measures like blacklisting wallets are unlikely to gain much popularity (although blacklists are not unheard of in the crypto space — as an example, NFT platforms recently froze trading for stolen NFTs) — even their limited adoption can make a difference, bringing more legitimate traffic to exchanges that go the extra mile.
Related: Major crypto exchanges eye Asian market amid growing regulatory clarity
In military terms, this is like waging a war of attrition against ransomware groups — wearing the enemy down as opposed to causing direct immediate damage. A sophisticated ransomware attack requires a hefty investment of time and money. This is true for both teams developing a tailored solution aimed at a specific high-profile target or an operator of a ransomware-as-a-service platform. Being unable to cash in on the ransom means most of that time, effort and investment just went into the trash bin.
Critics may argue that such measures wouldn’t work, simply because the hackers can always move to another financial mechanism for claiming their cash, such as gift cards. To an extent, this is true; where there’s a will, there’s a way. But consider this: Colonial Pipeline had to pay a ransom of $5 million in crypto to suspected Russian hackers. How easy would it have been for the attackers to cash in the same amount in Walmart gift cards? Would the risk-reward ratio still justify the attack? I doubt it. It makes sense to invest millions to steal billions, but moving these billions in anything but crypto without setting off a bunch of red flags is a whole different story.
Related: Are cryptocurrency ransom payments tax-deductible?
There is a better counter-argument here: Ransom is not always the motivation. A state-backed group striking as part of a larger adversarial campaign would appreciate the extra cash, but it’s just as interested in keeping its handlers happy. This is the pinch of salt that goes well with the pro-regulation argument, and yet, even denying ransom to financially-motivated hackers would already make a dent or two in the proliferation of ransomware.
All in all, ransomware is a complex problem, hard to solve with a single silver-bullet decision. It will require a more nuanced approach, and most likely, more international cooperation on the matter. There is nevertheless a strong case for making exchange regulation a major part of such efforts in a bid to deny attackers the ability to reap the fruits of their attacks — and thus go after the financial core of their operations.
This article does not contain investment advice or recommendations. Every investment and trading move involves risk, and readers should conduct their own research when making a decision.
The views, thoughts and opinions expressed here are the author’s alone and do not necessarily reflect or represent the views and opinions of Cointelegraph.
Lior Lamesh is the co-founder and CEO of GK8, a cybersecurity company that offers a self-managed end-to-end custodial platform with true cold vault and hot MPC capabilities for banks and financial institutions. Having honed his cyber skills in Israel’s elite cyber team reporting directly to the Prime Minister’s office, Lior oversees the development of GK8’s on-premises hardware and software.


















Comments (No)