Cybercriminals for the Democratic People’s Republic of Korea (DPRK) affirmed themselves as an advanced persistent threat to the cryptocurrency industry in 2021, Chainalysis reported.
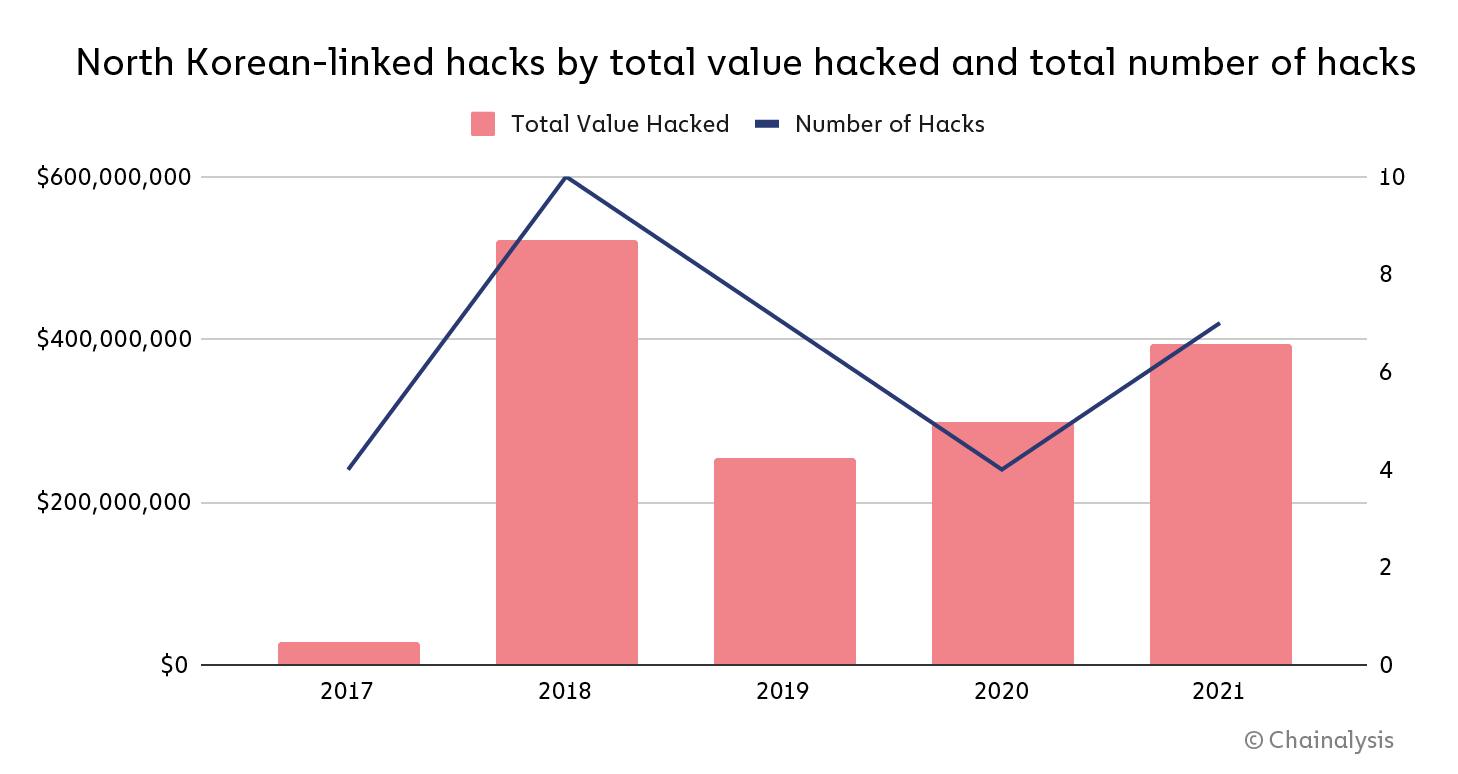
According to the blockchain-based data platform which supports government and private sectors in detecting and preventing the illicit use of cryptocurrencies, North Korean hackers stole $400 million worth of crypto last year, while the amount of total unlaundered funds stockpiled to an all-time high (ATH).
“Lazarus Group”
Targeting primarily investment firms and centralized exchanges, North Korean hackers launched at least seven attacks on cryptocurrency platforms–extracting almost $400 million worth of crypto in 2021.
While, compared to 2020, the number of attacks jumped from four to seven, the value extracted grew by 40%.

To siphon funds out of these organizations’ “hot” wallets into DPRK-controlled addresses, cybercriminals used phishing lures, code exploits, malware, and advanced social engineering.
Once North Korea gained custody of the stolen crypto, they used careful laundering tactics to cover up and cash out the funds.
“These complex tactics and techniques have led many security researchers to characterize cyber actors for the DPRK as advanced persistent threats (APTs),” the report noted, adding this is particularly true for APT 38, aka the “Lazarus Group,” led by DPRK’s primary intelligence agency, the US and UN-sanctioned Reconnaissance General Bureau
From 2018 on, Lazarus Group stole and laundered massive sums of cryptocurrencies each year–typically exceeding $200 million.
“The most successful individual hacks, one on KuCoin and another on an unnamed cryptocurrency exchange, each netted more than $250 million alone,” read the report, noting that, according to the UN security council, the revenue from the hacks supports North Korea’s WMD and ballistic missile programs.
Laundering process
In 2021, in terms of dollar value, Ethereum for the first time ever accounted for the majority of crypto stolen by DPRK, while Bitcoin accounted for only 20%, and ERC-20 tokens and altcoins accounted for 22% of the funds.
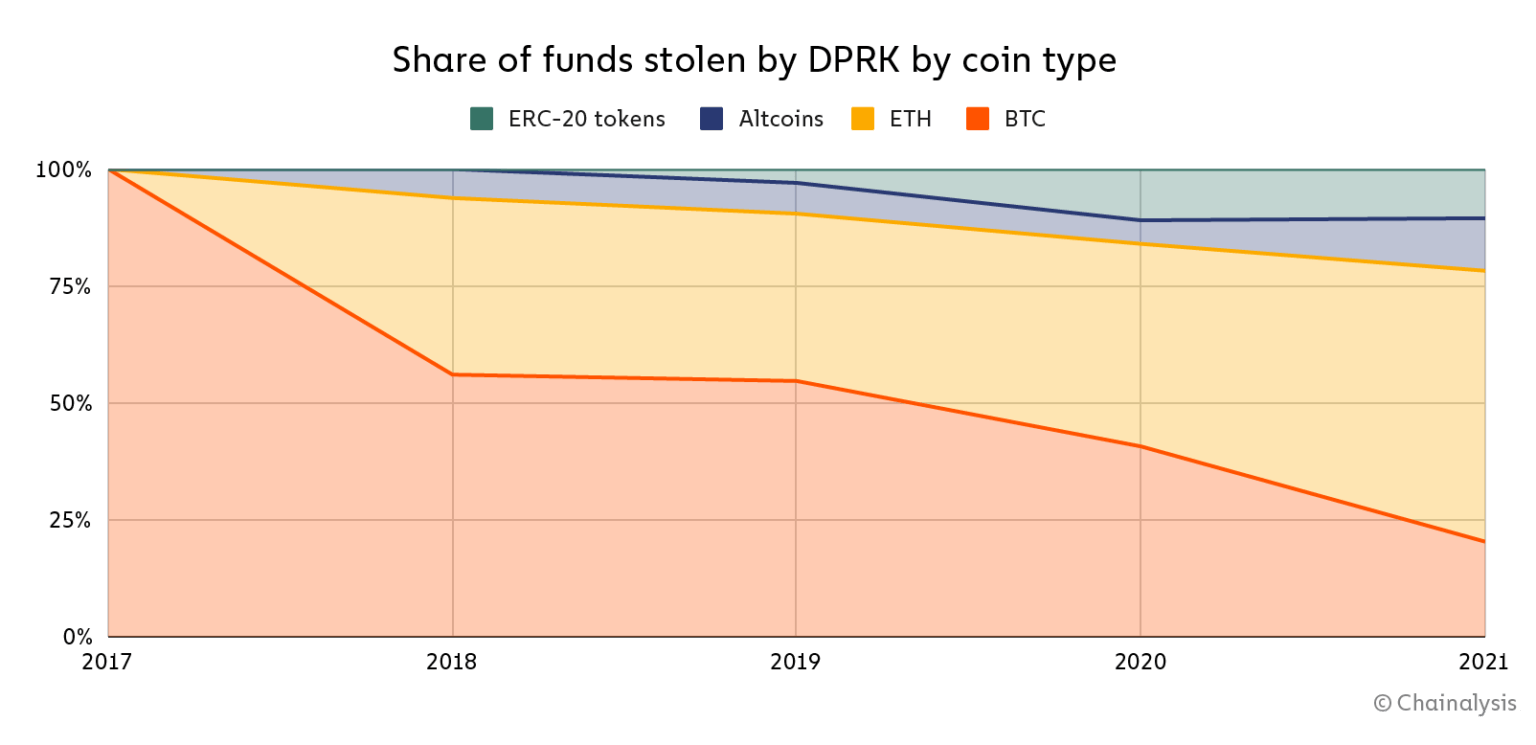

The growing variety of cryptocurrencies stolen led to the increased complexity of DPRK’s crypto laundering, according to Chainalysis, which broke down the sophisticated process into several steps, observing an increased use of ‘mixers’ among North-Korean hackers in 2021.
These software tools enable hackers to pool and shuffle cryptocurrencies from thousands of addresses and vastly complicate the tracking of transactions.
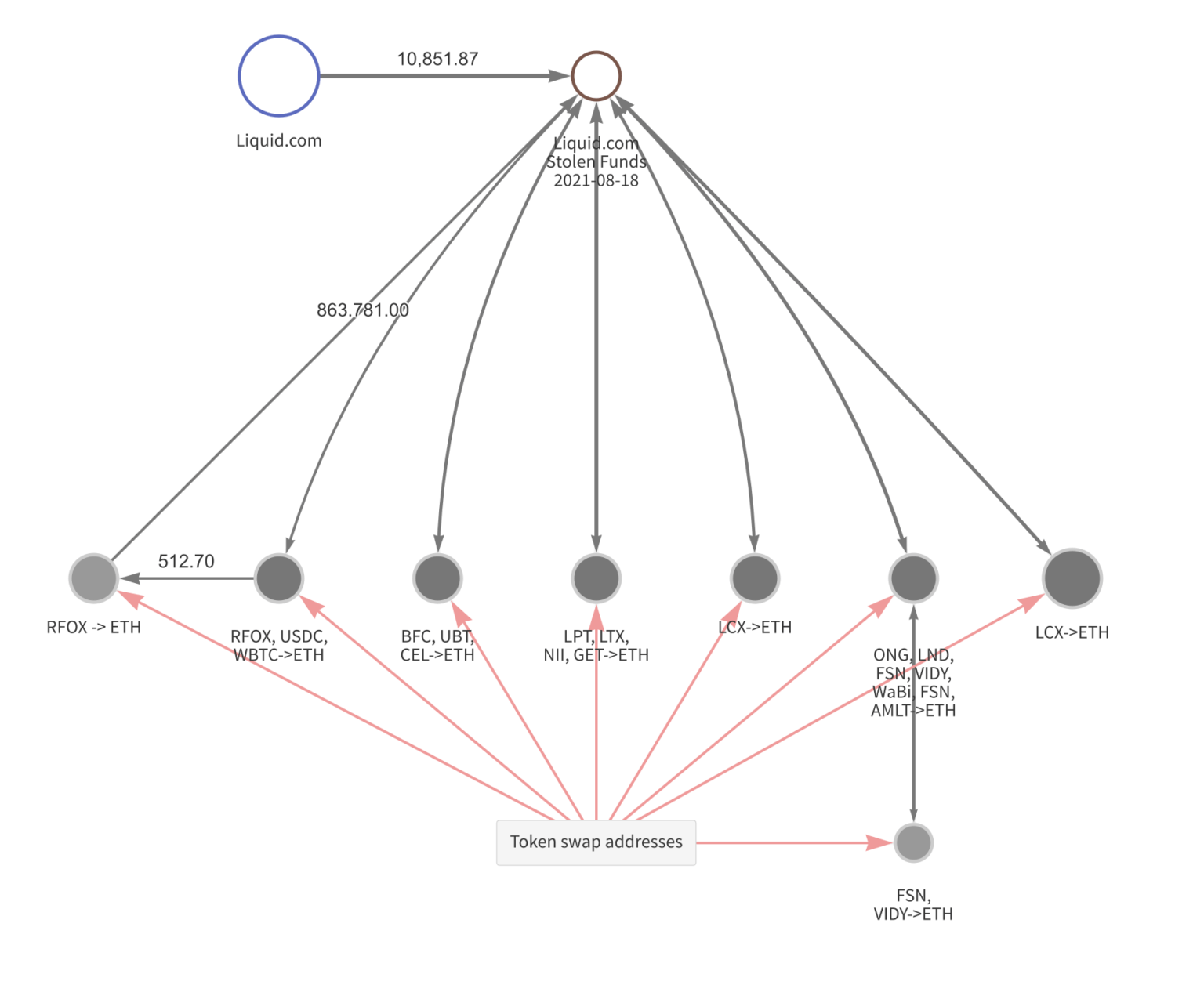
Chainalysis explained the currently used tactics based on one of the past years’ attacks–resulted in $91.35 million in crypto laundered.
In August, Liquid.com reported that an unauthorized user had gained access to some of the wallets managed by the crypto exchange. In the attack, 67 different ERC-20 tokens, along with large sums of Ethereum and Bitcoin were moved from these crypto wallets to addresses controlled by a party working on behalf of DPRK.
In a typically used laundering process, ERC-20 tokens and altcoins are swapped for Ethereum at DEXs.

In the next step, Ethereum is mixed and swapped for Bitcoin on DEXs and CEXs.
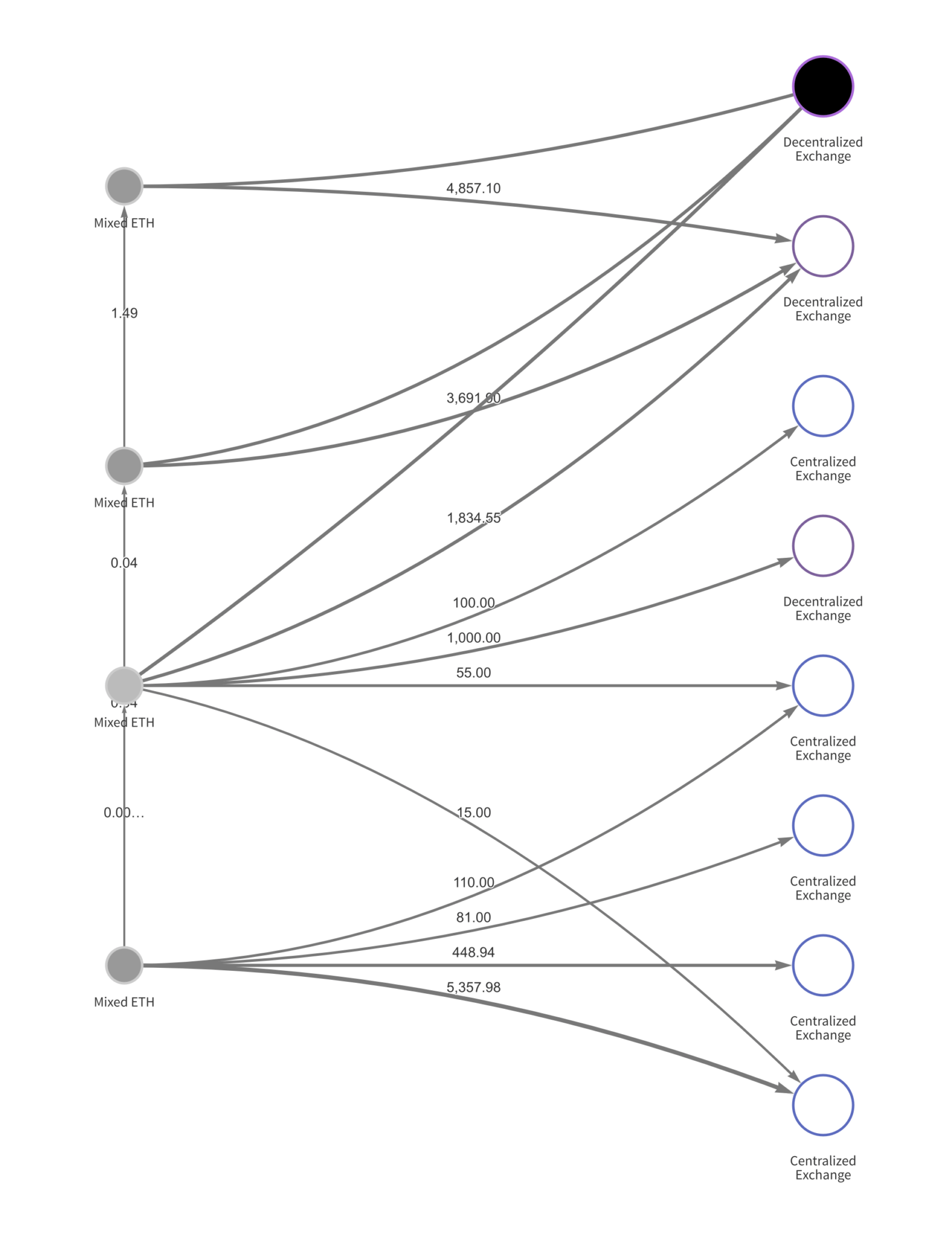

Finally, Bitcoin is mixed and consolidated into new wallets–after which it gets sent to deposit addresses at crypto-to-fiat exchanges based in Asia.
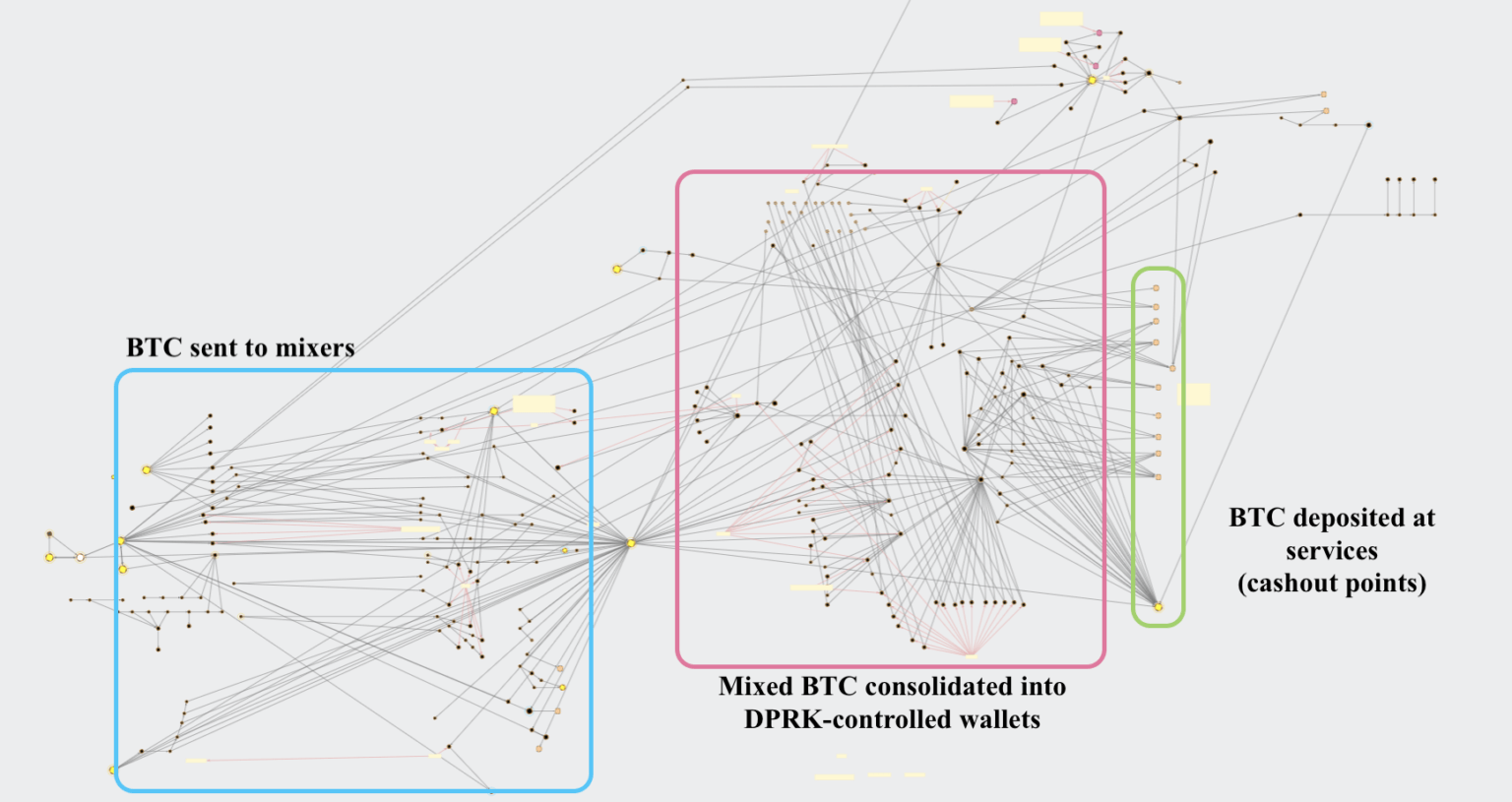

According to the report, more than 65% of DPRK’s stolen funds were laundered through mixers in 2021, up from 42% in 2020.
Chainalysis describes DPRK’s use of multiple mixers as a “calculated attempt to obscure the origins of their ill-gotten cryptocurrencies while off ramping into fiat.”
Meanwhile, DPRK hackers resort to DeFi platforms like DEXs to “provide liquidity for a wide range of ERC-20 tokens and altcoins that may not otherwise be convertible into cash.”
Swapping these cryptos for Ethereum or Bitcoin makes them not only more liquid, but opens up a greater choice of mixers and exchanges.
Being non-custodial, DeFi platforms often don’t collect know-your-customer (KYC) information, which enables hackers to use their services without having their assets frozen or their identities exposed, according to Chainalysis.
Unlaundered funds stockpiling
“Chainalysis has identified $170 million in current balances–representing the stolen funds of 49 separate hacks spanning from 2017 to 2021–that are controlled by North Korea but have yet to be laundered through services,” read the report.
The report revealed massive unlaundered balances as much as six years old–approximately $35 million of DPRK’s total holdings came from attacks in 2020 and 2021, while more than $55 million came from attacks carried out in 2016.
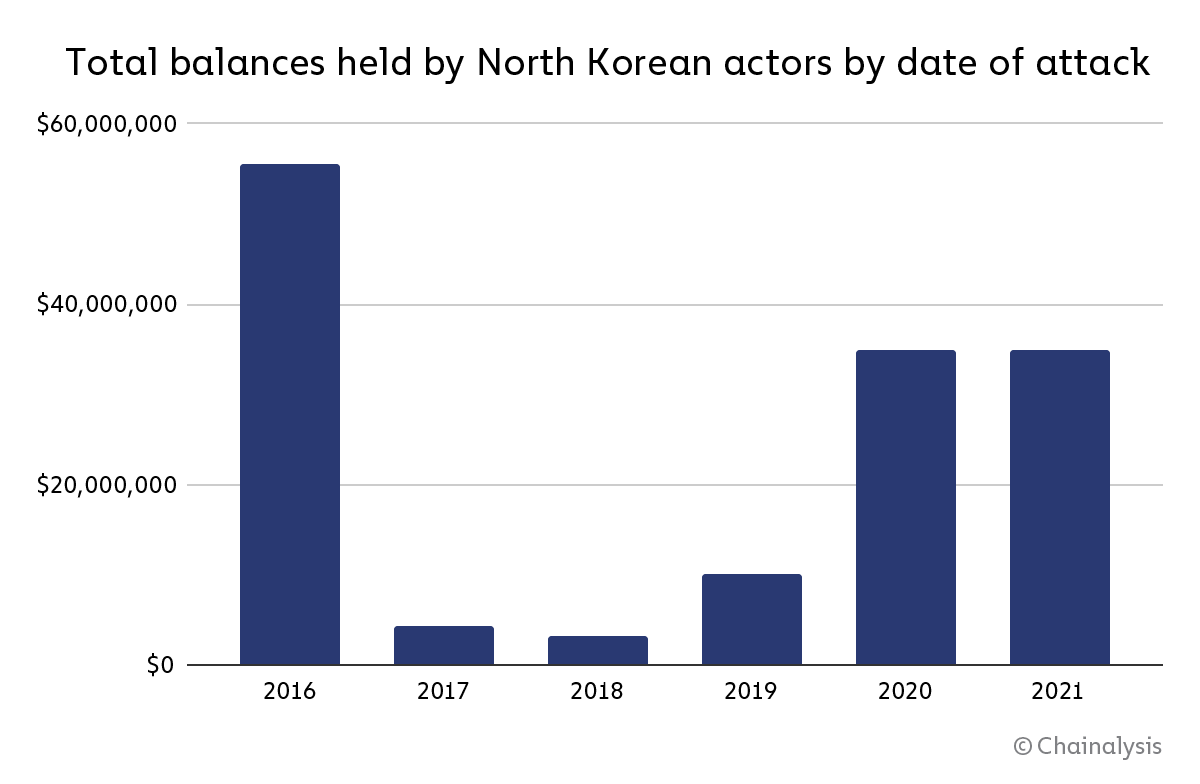

“It’s unclear why the hackers would still be sitting on these funds, but it could be that they are hoping law enforcement interest in the cases will die down, so they can cash out without being watched,” read the report, adding that whatever the reason “the length of time that DPRK is willing to hold on to these funds is illuminating because it suggests a careful plan, not a desperate and hasty one.”
CryptoSlate Newsletter
Featuring a summary of the most important daily stories in the world of crypto, DeFi, NFTs and more.
Get an edge on the cryptoasset market
Access more crypto insights and context in every article as a paid member of CryptoSlate Edge.
On-chain analysis
Price snapshots
More context


















Comments (No)