Earlier this month, Check Point Research alerted NFT marketplace Rarible regarding a major security flaw on the platform. The research team then worked closely with Rarible to install an immediate fix. This could have been a major heist if it was exploited, as the threat actor can steal a user’s NFTs and crypto tokens in a single transaction.

Malicious NFTs Hiding in Plain Sight
Earlier this month, Taiwanese singer songwriter and producer, Jay Chou had his Bored Ape and other NFTs swept away in an NFT heist. This motivated Check Point Research (CPR) to unearth similar threats hiding in plain sights. Fortunately, the team discovered the malicious NFTs on Rarible before it could be exploited. Such threats are worse than phishing attacks as users usually lower their guard on trusted marketplaces such as Rarible.
Basically, the NFT has a EIP-721 token standard, which provides basic functionality to track and transfer NFTs. However, this standard also has a function called ‘setApprovalForAll’, where 3rd parties like Rarible and OpenSea can control digital assets on behalf of the users. As users typically do not read the details when they sign a transaction, they could have easily signed away all their assets to the hacker.
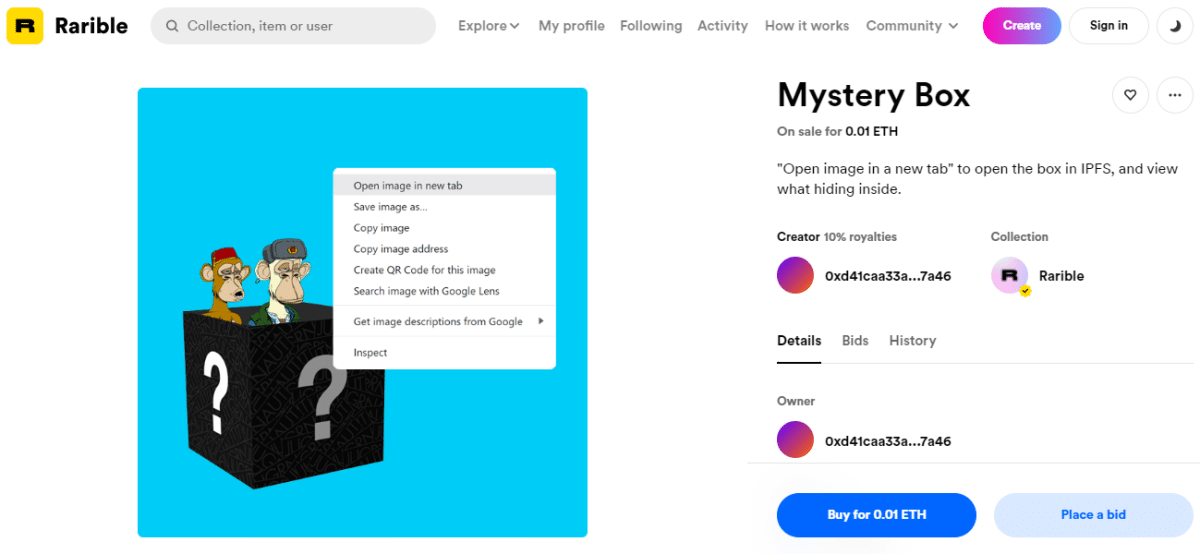
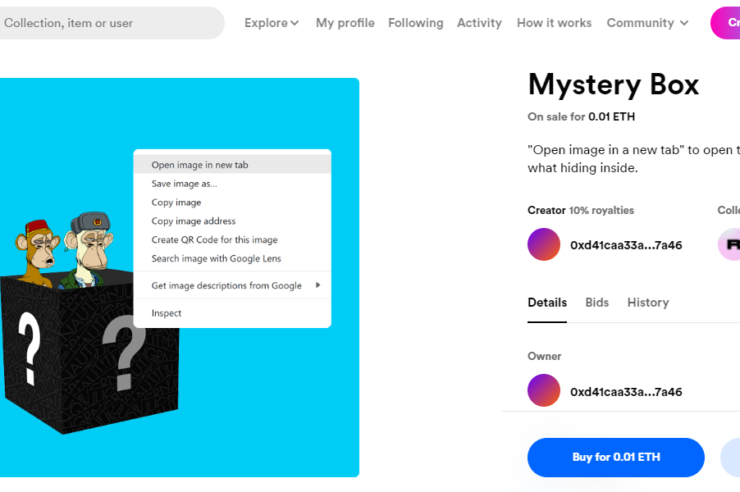
Check Point Research created a simple SVG file to demonstrate how easy it is to sneak an attack into the platform. By clicking on the art and opening it in another tab, or by pressing on the IPFS link from the drop-down, the JavaScript code will be executed. After the hacker gets access to the account, he can then easily use the ‘transferFrom’ action to wipe the account clean.
Check Point Research Safety Tips
CPR is a research team that provides leading cyber threat intelligence to their clients and the crypto community in general. In essence, they collect and analyze global cyber attack data stored on ThreatCloud. CPR will continue to discover new cyber threats and develop the threat intelligence community to protect the entire industry.
After this recent discovery, the company strongly recommends the following precautions. Firstly, users should always be careful and aware whenever they receive requests to sign any links. This applies for any marketplace and crypto exchanges. Before signing anything, users need to review the request, and determine if it can potentially be malicious.
It can be tempting to quickly sign a request when you’re in the middle of a gas war. Nevertheless, users should reject a request if there is the slightest bit of suspicion, and only accept after adequate examination. Lastly, the Ethereum Token Approval facility allows users to review and revoke any past token approvals to secure the accounts.
Are you tired of missing important NFT drops?
Just check out our NFT Calendar!
Receive the biggest NFT news of the day & recommendations in our Daily newsletter.
All investment/financial opinions expressed by NFTevening.com are not recommendations.
This article is educational material.
As always, make your own research prior to making any kind of investment.

















Comments (No)