Ethereum co-founder Vitalik Buterin has published a research paper diving into privacy pools systems as a tool to achieve more privacy in financial transactions, allowing users to prove dissociation from illicit funds through zero-knowledge proof technology.
The document initially discusses one of the most popular privacy-enhancing protocols, Tornado Cash, which allows users to deposit and withdraw cryptocurrencies without creating an identifiable link between the two addresses. Recently, United States authorities filed criminal charges against its founders, alleging extensive use by bad actors.
“The critical issue with Tornado Cash was essentially that legitimate users had limited options to dissociate from the criminal activity the protocol attracted,” reads the paper co-authored by Jacob Illum, Matthias Nadler, Fabian Schar and Ameen Soleimani.
The analysis then elaborates on an extension of Tornado Cash’s approach that would enable users to publicly prove the source of funds on-chain by allowing membership proofs — “I prove that my withdrawal comes from one of these deposits” — and exclusion proofs — “I prove that my withdrawal does not come from one of these deposits.”
According to the authors, the concept could provide a balance between honest and dishonest protocol users, potentially enabling financial compliance on-chain in the future:
“The core idea of the proposal is to allow users to publish a zero-knowledge proof, demonstrating that their funds (do not) originate from known (un-)lawful sources, without publicly revealing their entire transaction graph. This is achieved by proving membership in custom association sets that satisfy certain properties, required by regulation or social consensus.”
With Privacy Pools, users can exclude themselves from anonymity sets that include addresses related to illegal activities based on zero-knowledge proofs — a method of proving a statement without disclosing the statement’s details.
The underlying idea presented in the document asserts that instead of simply using zero-knowledge to prove that a “withdrawal is linked to some previously-made deposit, a user proves membership in a more restrictive association set.”
The association set can include all previously made deposits, only the user’s own deposits, or anything in between. As a public input, the user specifies the set by providing its Merkle root. “For simplicity, we do not directly prove that the association set actually is a subset of the previously-made deposits; instead, we just require the user to zero-knowledge-prove two Merkle branches.”
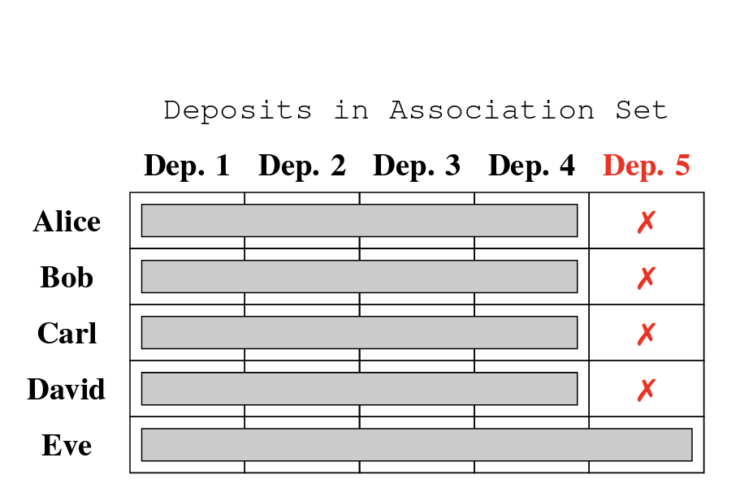
To illustrate it in a law enforcement context, the authors provide a simple example:
“Suppose that we have five users: Alice, Bob, Carl, David and Eve. The first four are honest, law-abiding users who nevertheless want to preserve their privacy, but Eve is a thief. Suppose also that this is publicly known.”
In the example, when one of the users wants to withdraw funds, they can specify which association set they want, meaning they are incentivized to make their association sets larger to safeguard privacy. However, to avoid their funds from being perceived as suspicious by merchants or exchanges, the users do not include Eve in their association set. Eve, however, cannot exclude her own deposit, and will be forced to make an association set equal to the set of all five deposits.

“[…] we assume that Alice, Bob, Carl and David include all other “good” deposits in their respective association sets and exclude deposit 5, that originates from a known illicit source. Eve, on the other hand, cannot create a proof that disassociates her withdrawal from her own deposit.”
According to the authors, the example illustrates one possibility for the use of association sets in privacy pools protocols. “Note, that the system does not rely on altruism on Alice, Bob, Carl and David’s part; they have a clear incentive to prove their disassociation.”
The paper further offers several other use cases of zero-knowledge-proof for users to demonstrate that funds are not tied to illicit sources or to prove that funds originate from a specific set of deposits without revealing any further information.
“In many cases, privacy and regulatory compliance are perceived as incompatible. This paper suggests that this does not necessarily have to be the case, if the privacy-enhancing protocol enables its users to prove certain properties regarding the origin of their funds.”
Protocols working on zero-knowledge solutions are on the rise, with the Ethereum network dominating major launches, according to a recent research. The findings point out that scaling zk-proof solutions are set to experience the highest growth in the coming 12 months, as global regulations evolve and users seek to protect their privacy.
Magazine: Recursive inscriptions — Bitcoin ‘supercomputer’ and BTC DeFi coming soon

















Comments (No)