To safeguard against known-plaintext attacks, adopt strong encryption algorithms, manage encryption keys securely, use unique keys per session, and add randomness to encryption processes to enhance protection against attacks.
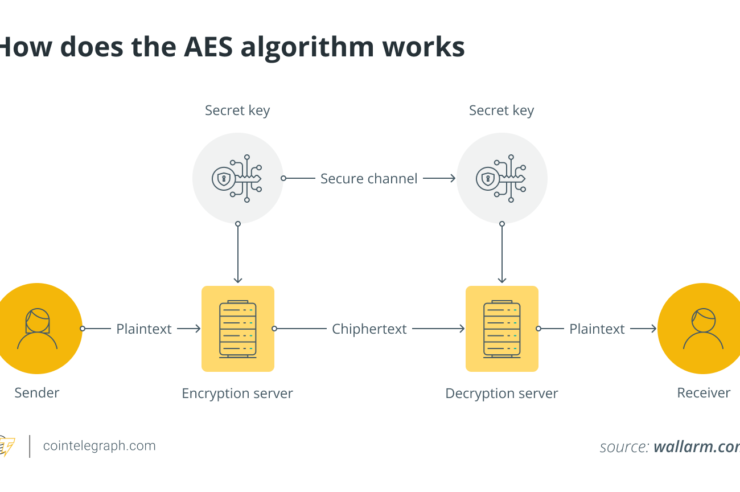
Choose encryption algorithms that can withstand known-plaintext attacks by using strong encryption techniques. By preventing patterns in the plaintext from correlating with patterns in the ciphertext, modern cryptographic algorithms like the Advanced Encryption Standard (AES) are made to survive such attacks. AES is a widely used symmetric encryption algorithm known for its security and efficiency.

Securely manage encryption keys to avoid unauthorized access. Use secure key repositories, rotate your keys frequently and use strong key generation techniques. Additionally, avoid encrypting discrete, predictable chunks of data. To stop an attacker from using known pairs, encrypt the entire message or file.
Moreover, use various keys for various sessions and endeavors. The impact of a known-plaintext attack is reduced because each session will use a different encryption key. Also, maintain the most recent versions of your systems, libraries and encryption software. Security fixes that repair vulnerabilities are frequently included in updates.
Before encrypting the plaintext of the data, add a cryptographic salt — a random value — to it. This makes each encryption unique, even when encrypting the same plaintext multiple times. In addition, avoid encryption methods that are known to be vulnerable to known-plaintext attacks. That said, perform proper due diligence when selecting encryption algorithms.


















Comments (No)